Log4j Remote Code Execution Vulnerability (CVE-2021-44228)
Related Products_
- Advanced EPDR
- Advanced EDR
Description
On 9 December 2021, researchers disclosed a critical, unauthenticated remote code execution (RCE) vulnerability (CVE-2021-44228) in version 2 od Log4j, a popular and widely-used logging library for Java applications. An attacker could exploit this vulnerability to run untrusted code on vulnerable systems.
There are several mitigating factors, including the version of Java the application uses with JDK versions newer than 6u11, 7u201, 8u191 and 11.0.1 not affected by the common and trivial LDAP attack vector. Additionally, Log4j implementations that have explicitly disabled JNDI lookups are not vulnerable.
After a thorough analysis, WatchGuard has determined that none of the WatchGuard/Panda products and services are vulnerable to the trivial LDAP attack vector. Some services and service middleware were found to run a vulnerable version of Log4j but paired with a non-vulnerable JDK version. We have proactively patched these services and have found no evidence of successful exploits against these services.
For more information, see this Secplicity blog post.
How to identify vulnerable computers and servers
If you have any of Advanced EPDR/EDR solutions, simply launch an on-demand scan on all Windows, macOS and Linux computers in your company and any software affected by the Log4j vulnerability will be detected.IMPORTANT: It is recommended to launch the scan during off-peak hours because, although the scans are launched with low priority to minimize consumption, the continuous reading of files on disk may have a slight impact on the performance of the computer or server.The detections will be displayed in the Threats detected by the antivirus widget and list.
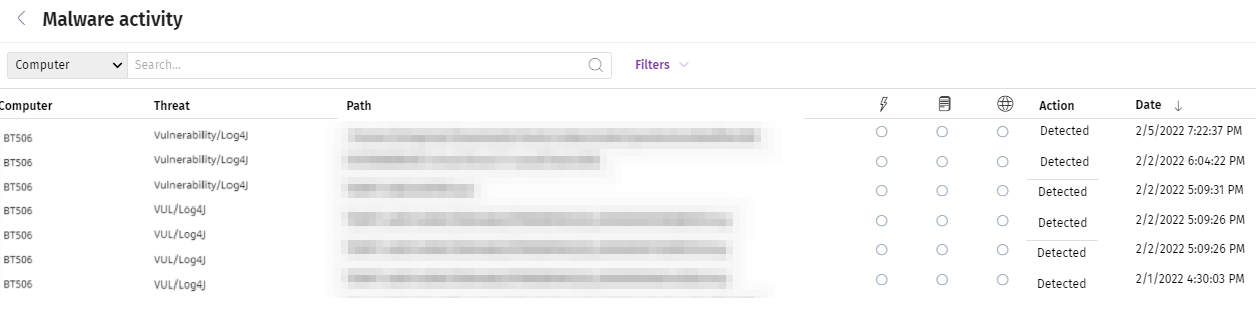
And in the computer’s Details screen:
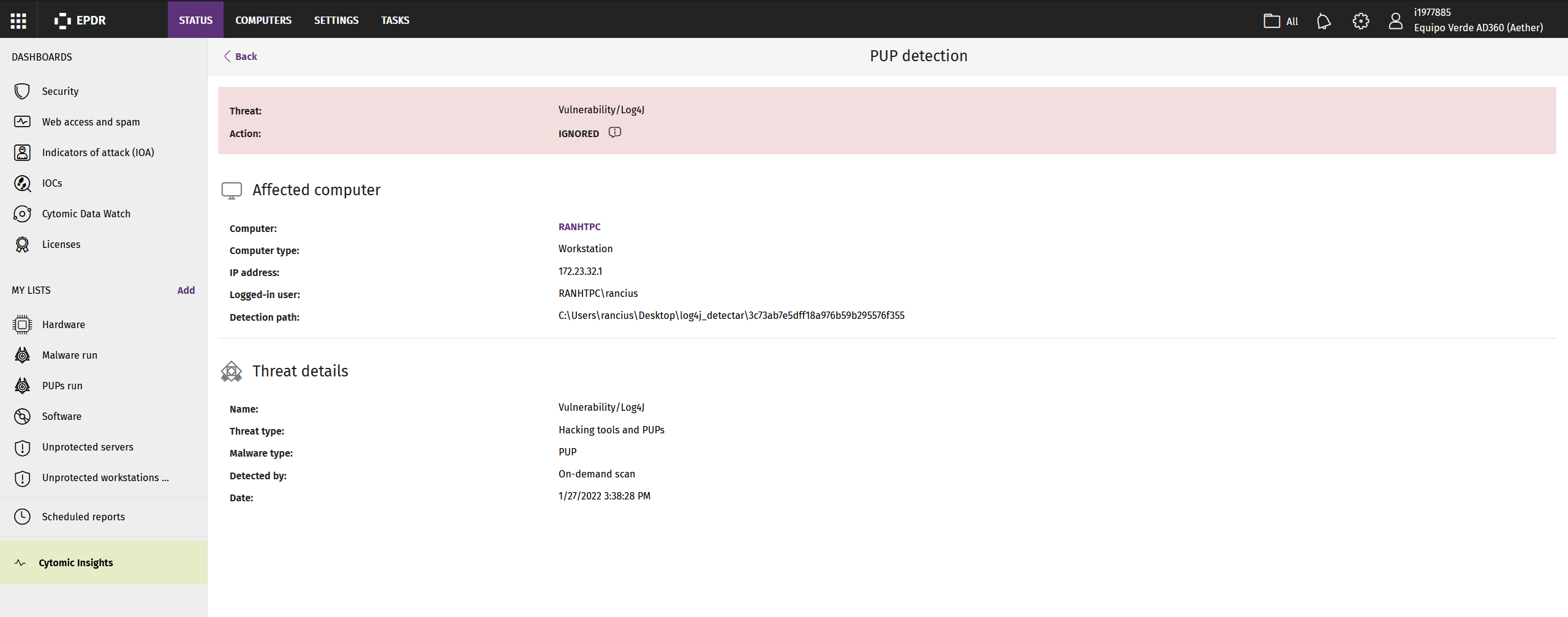
Once the computers and files affected by the vulnerability have been identified, immediately update the Log4j component and ensure that JNDI searches are disabled by setting the JVM flag log4j2.formatMsgNoLookups to True to mitigate the vulnerability.
If you have vulnerability scanning and patching tools such as Cytomic Patch, make sure that the vulnerability identified with CVE-2021-44228 is not found on your computers or servers, and, if not, patch it as soon as possible.
