What is Network Access Enforcement and how to configure it in Advanced EPDR/EDR
Related Products_
- Advanced EPDR
- Advanced EDR
Introduction
Network Access Enforcement provides an additional layer of protection when user computers connect to the corporate network either remotely using a VPN connection or locally using a Wi-Fi connection.
A user computer trying to connect to a corporate network using a VPN or a Wi-Fi connection must meet a series of requirements for the connection to be allowed. If it does not meet those requirements, the connection is rejected.
The Cytomic agent installed on the computer collects and sends the information required by the device that performs the necessary checks: Firebox for VPN connections and Access Point for Wi-Fi connections.
UUID validation
A UUID (Universal Unique Identifier) is a character string used to uniquely identify a device.
The device (Firebox or Access Point) uses UUID and authentication key to validate VPN and Wi-Fi connections. Therefore, you must have configured the same UUID and authentication key pair on the device and on the Advanced EPDR console.
If you have not configured a UUID on the device, you must generate a new one. UUID is an open format so you can use free tools such as https://www.uuidgenerator.net/
Use a long password that includes upper case, numeric, and special characters.
For more information about the Firebox and its VPN connection settings, see this article.
Requirements
For a user computer to connect to a corporate network, it must meet these requirements:
- The computer must have the security software installed, running, and correctly configured.
- You must have a valid UUID and authentication key configured on the device that validates the connection and on the Advanced EPDR console.
- Operating system: Windows 8.1 or higher, macOS High Sierra 10.13 or higher.
- Ports: For the security protection for VPN connections to work properly, the agent installed on the computer requires port 33000 for its communication with the Firebox.
- Activated and running advanced hardening or lock mode protection.
- Activated and running antivirus protection is considered valid.
Network Access Enforcement is not compatible with Linux.
When you enable this functionality, computers running these operating systems or versions earlier than Windows 8.1 will not be able to connect to the VPN.
Requirements check
When a computer tries to connect to a corporate network, the device that validates the connection takes these actions:
- Requests information about the status of the protection installed on the computer.
- Verifies the account UUID and the authentication key are valid.
- Verifies the computer operating system against the operating systems defined in the device settings.
If all checks turn out positive, the device allows access from the computer to the corporate network. Otherwise, it rejects the connection.
NOTE: By default, all computers are forced to comply with the security requirements for connecting to the corporate network.
Access to security settings for VPN connections
To turn on security for VPN connections, follow these steps:
- Click Network Services in the side menu.
- In the top tab menu, click Network Access Enforcement.
- To turn protection on, turn on the slider.
- Enter the UUID of the account and the authentication key.
- Click the Save Changes button.
Configure Secure VPN on the Firebox
Until the release of Fireware v12.9, you configure secure VPN for the Firebox with the TDR host sensor enforcement settings in Fireware Web UI or Policy Manager.
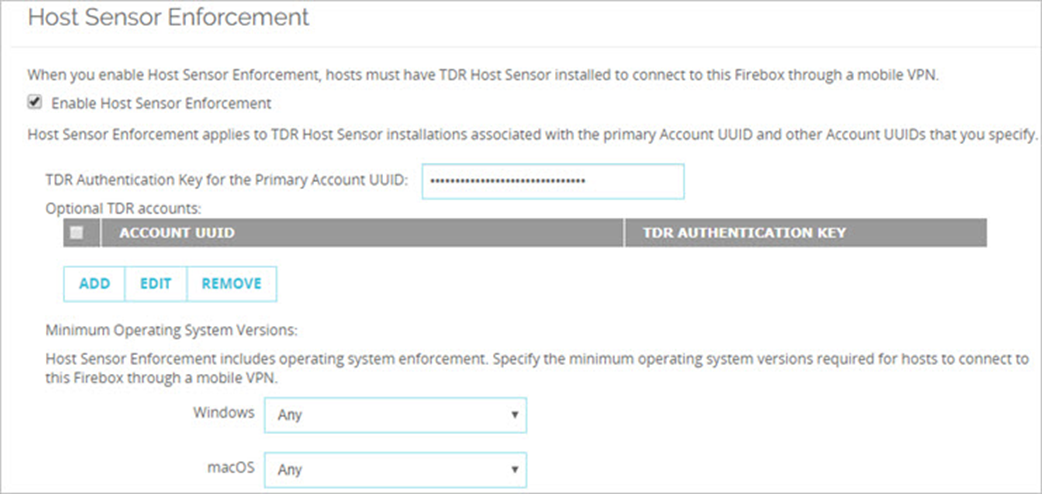
For information on how to configure host sensor enforcement on the Firebox, see Configure TDR Host Sensor Enforcement in Help Center.
