Cytomic Patch Best Practices
Related Products_
- Cytomic EPDR
- Cytomic Patch
Introduction
We recommend you follow these best practices for Cytomic Patch Management:
- Verify that Cytomic Patch Works Properly
- Install All Critical Patches Regularly
- Isolate Vulnerable Computers
- Make Sure Programs Installed on your Computers are Not End-of-Life
- Check the Installation History
- Check the Patch Status of Computers where Incidents Occurred
Verify that Cytomic Patch Works Properly
- To confirm that Cytomic Patch works correctly, make sure that all computers on your network:
- Have a Cytomic Patch license allocated and Patch Management installed and running. To identify issues, use the Cytomic Patch Status tile on the Cytomic Patch Dashboard.
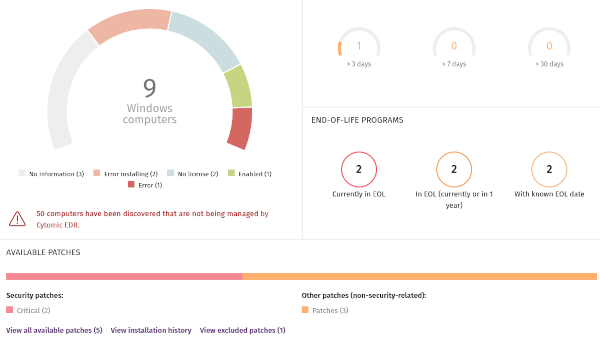
- Can communicate with the Cytomic server. To identify computers that might have connection problems, use the Time Since Last Check tile on the Cytomic Patch Dashboard.
- Have the Windows Update service running with automatic updates disabled. To disable automatic updates, select the Disable Windows Update on Computers option in the Patch Management Settings.
- Have a Cytomic Patch license allocated and Patch Management installed and running. To identify issues, use the Cytomic Patch Status tile on the Cytomic Patch Dashboard.
Install All Critical Patches Regularly
When software vendors discover flaws in their products, they publish updates and patches to fix the flaws. We recommend that you install critical patches at least once a month.
To see available patches, use the Available Patches list. Filter the list to identify critical patches or patches for specific computers.
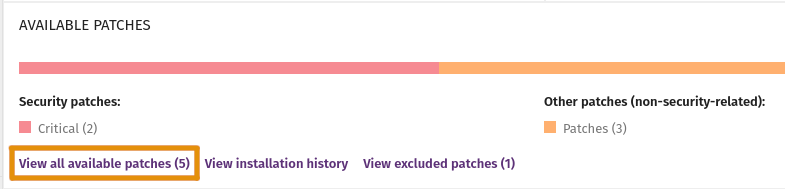
If Cytomic Patch cannot get a download URL to install a critical patch automatically, download the patch manually so you can install it.
Isolate Vulnerable Computers (only for critical situations)
Identify and isolate computers that have not yet received published patches that fix critical known vulnerabilities.
IMPORTANT! This feature is only to be used for critical security issues.
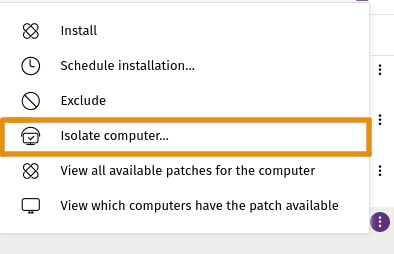
Use the Available Patches list to identify computers that have not received critical patches. To isolate computers, select the check box in one or more rows, then in the toolbar, click Isolate Computer.

Make Sure Programs Installed on your Computers are Not End-of-Life
End-of-life programs do not receive patches or updates from the software vendor. To reduce the attack surface, replace any end-of-life programs installed on your computers.
To identify end-of-life programs, use the End-of-Life Programs list.

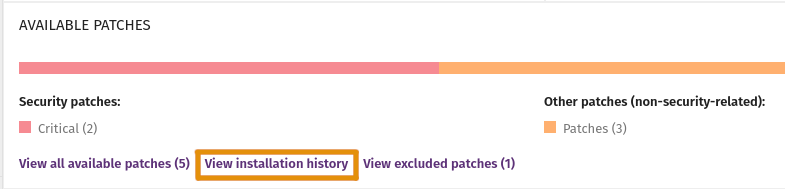
Check the Installation History
Use the Installation History list to review the status of patch installations and identify computers where installation errors occurred.
Check the Patch Status of Computers where Incidents Occurred
When incidents occur on a computer, we recommend that you install any available patches on the computer.
To identify available patches, in the Security Dashboard, click a threat, select the affected computer, and then click View Available Patches. The Available Patches list opens and shows available patches for the computer.
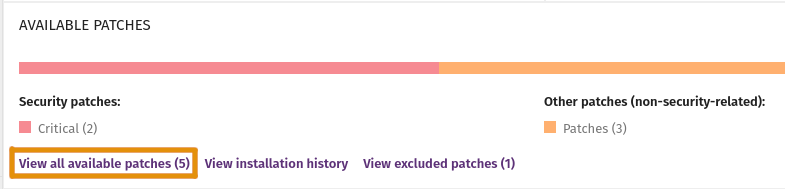
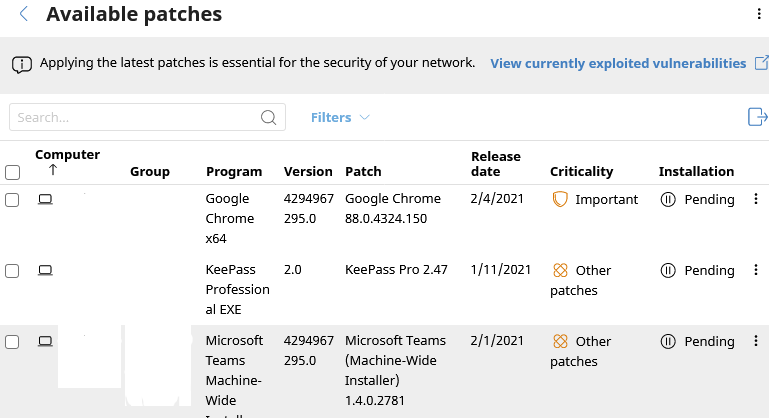
You can also see an overview of available patches and end-of-life programs for a computer on the Computer Details page.
