Installation of the Advanced EPDR/EDR client software on Linux platforms with Secure Boot
Related Products_
- Advanced EPDR
- Advanced EDR
Situation_
Some Linux distributions return protection errors that you can see in the computers’ details screen when Secure Boot is enabled and you try to install the protection or when the protection is installed and you try to enable Secure Boot.
Solution_
To solve these errors, you must update the protection repository and then register the Panda protection keys from the command line.
IMPORTANT!
Make sure that you meet these system requirements beforehand:
- DKMS: mokutil and openssl packages.
- Oracle Linux 7.x/8.x with kernel UEKR6:
- Repository ol7_optional_latest enabled.
- openssl, keyutils, mokutil, pesign, kernel-uek-devel-$(uname -r) packages.
Solution
Follow these steps to solve the protection errors related to Secure Boot from the computer experiencing the problem.
- Check the state of Secure Boot:
$ mokutil –sb-state
Secure Boot enabled - Verify that the driver is not loaded:
$ lsmod | grep prot - Import the protection keys:
$ sudo /usr/src/protection-agent-<version-number>/scripts/sb_import_key.sh
IMPORTANT: The agent and protection have this format:
protection-agent-03.01.00.0001-1.5.0_741_g8e14e52 (the name varies according to the version and the driver).You will see a message informing of the implications of using Secure Boot. - Press C to register the certificate used to sign the modules.
- Create an 8-character password:
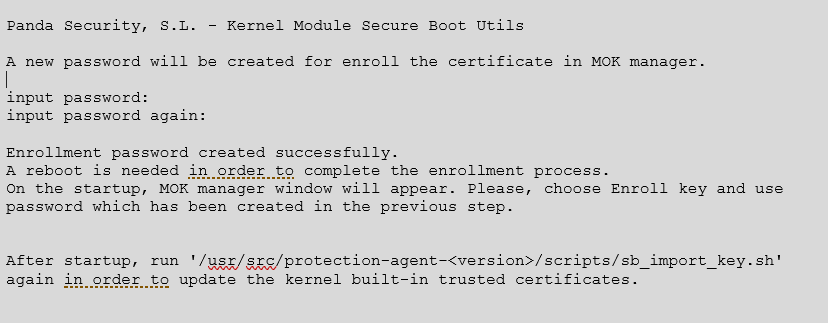
- Restart the computer and complete the registration process.
If it is a virtual machine, use the hypervisor.- Press any key to start the registration process. This screen appears for a limited time, so if no keys are pressed, you must restart the registration process.
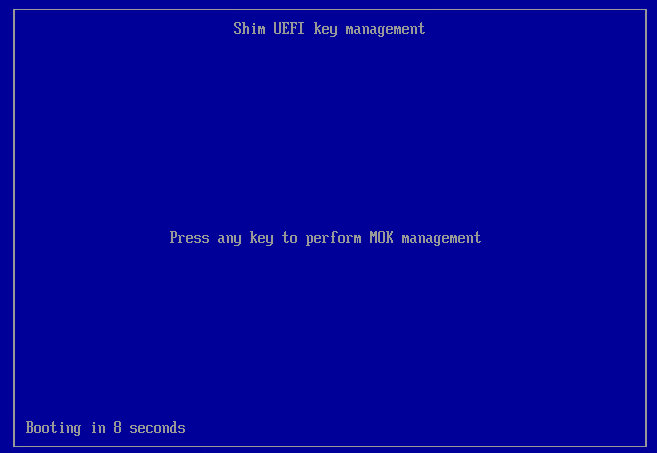
- Select Enroll MOK.
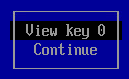 Select View key to view the keys that are going to be registered.
Select View key to view the keys that are going to be registered. 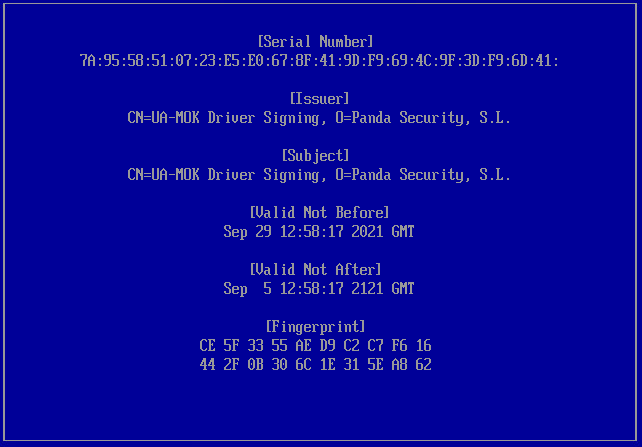
- Check that the keys belong to the Cytomic protection, and select Continue to resume the registration process.
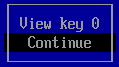
- When prompted Enroll the key, select Yes.
- Then, enter the password chosen previously.
- Select Reboot to finish the procedure.
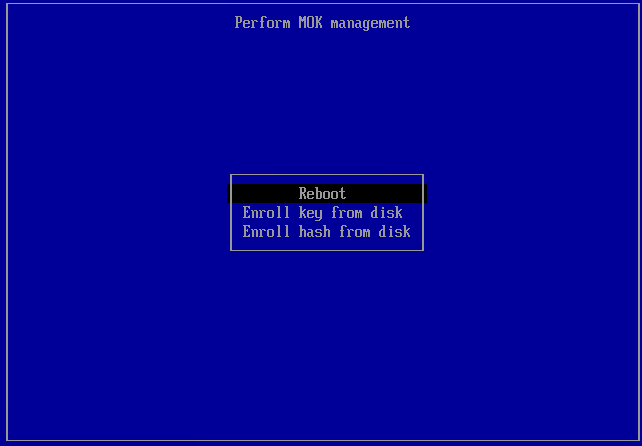
- Press any key to start the registration process. This screen appears for a limited time, so if no keys are pressed, you must restart the registration process.
- Finally, check that the driver is loaded:
$ lsmod | grep prot
protection_agent 184320
After the general procedure is complete, if the distribution installed is Oracle Linux 7.x/8.x with UEKR6 kernel, follow these additional steps:
- Run this command again:
$ sudo /usr/src/protection-agent-<version-number>/scripts/sb_import_key.sh
This adds the certificate used to sign the modules to the list of certificates trusted by the kernel. The modified kernel is signed and added to the list of kernels in GRUB. - Restart the computer.
- The module is loaded and started.
- To ensure that the certificate has been added correctly, run this command:
$ sudo /usr/src/protection-agent-<version-number>/scripts/sb_import_key.sh
The result is:
The signer´s common name is UA-MOK Driver Signing
Image /boot/vmlinuz-kernel-version-panda-secure-boot already signed
Kernel module succesfully loaded
