How does Remote Control work in products based on Advanced EPDR/EDR?
Related Products_
- Advanced EPDR
- Advanced EDR
Introduction
The Remote Computer Control enables you to remotely connect to the computers on your network from the web console to check their status or start troubleshooting tasks.
Required permissions
- To view and modify the remote control settings, the user account must have the Configure remote control permission.
- To remotely access computers on the network, the user account must have the Remote computer control permission.
Requirements
Remote control is available for computers with a Windows operating system installed.
In order for you to use the remote access and remote command line tools, the user computer and the network perimeter firewall must allow traffic to and from the following URLs:
- dir.rc.pandasecurity.com through port 443
- eu01.rc.pandasecurity.com through ports 8080 and 443
- eu02.rc.pandasecurity.com through ports 8080 and 443
- eu03.rc.pandasecurity.com through ports 8080 and 443
- eu04.rc.pandasecurity.com through ports 8080 and 443
- eu05.rc.pandasecurity.com through ports 8080 and 443
- eu06.rc.pandasecurity.com through ports 8080 and 443
- ams01.rc.pandasecurity.com through ports 8080 and 443
- ams02.rc.pandasecurity.com through ports 8080 and 443
Remote Control Settings
To enable remote control for the computers on the network, you must assign a settings profile to the computers you want to access. Here you can read de description of every option:
- Click the Settings menu at the top of the console. Select Remote control from the side menu. A page opens that shows the existing remote control settings profiles.
- Click Add in the upper-right corner of the page. The Add settings page opens.
- In the Name text box, type a name for the settings profile. In the Description text box, type a description of the profile (optional).
- Click Save.
- Click the No recipients selected yet link. Choose the computers or computer groups on the network that will receive the remote control settings profile.
- Configure the remote control feature you want to enable for the computers affected by the profile:
- Terminal: Remote access to the Windows console terminal.
- Process monitor: Remote monitoring of Windows processes.
- Service monitor: Remote configuration of Windows services.
- File transfer: Remote transfer of files to or from your computer.
- Click Save in the upper-right corner of the page. The profile is assigned to the target computers and you can establish remote control sessions to them.
Accessing the Remote Control feature
You can establish a remote control session from the context menu of the target computer or of a list. Select Remote control. This option is available in the following lists:
- Licenses
- Hardware
- Risks by computer
- Computer protection status
- Encryption status
- Patch management status
- Data Control status
- Computer list
Remote Control tool description
- Process manager
The Process manager shows all processes loaded in the computer memory and enables you to find, stop, and launch specific processes remotely. It also gives details of the RAM and CPU used by each process.
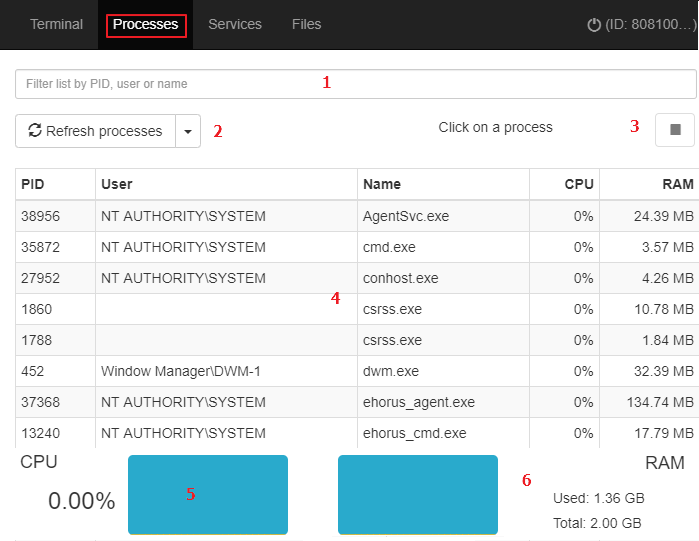
- Service manager
The Service manager shows all services configured on the computer and enables you to find specific services and change their status.
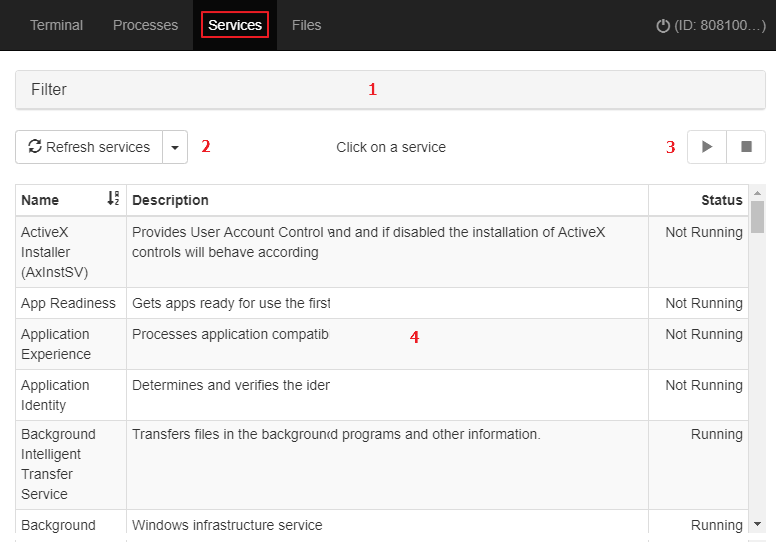
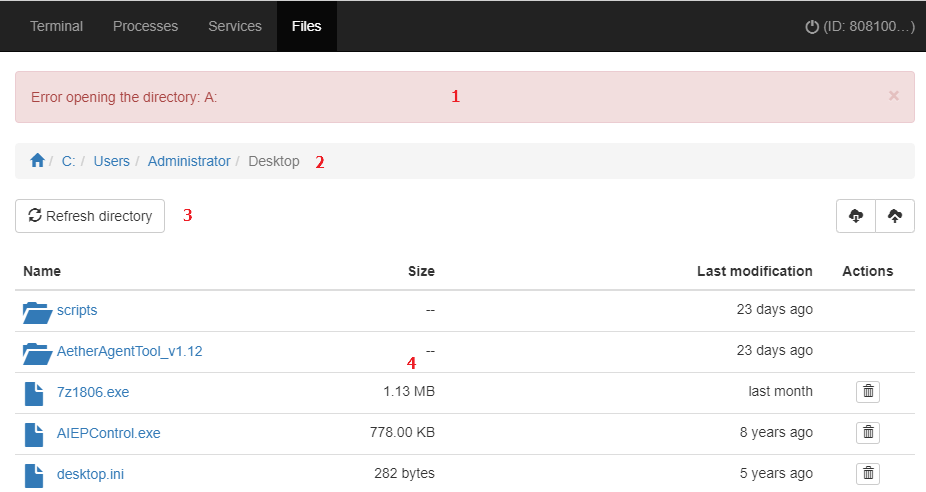
- File transfer
The File manager enables you to transfer files from your computer to a remote computer and vice versa. It also enables you to navigate the remote computer’s file system and delete files.
Remote Command line
Enables you to run commands compatible with the cmd.exe interpreter on the remote computer and launch programs that generate text output. It runs under the LOCAL_SYSTEM account on the remote computer and is installed on the following path:
C:\Program Files (x86)\Panda Security\Panda Aether Agent\Remote access\
includes the rt.exe program, which provides access to a set of tools that help you respond to security incidents. These tools enable you to recover information to perform a subsequent forensic analysis, and restore devices affected by a security breach to their original state.
You can access the rt.exe program from the remote command line. The program has the following syntax:
rt.exe [command] [-h|–help]
The following points affect the rt.exe command:
- command indicates an action to take. Each one supports different parameters.
- Wildcards “*”, “?” are not supported.
- Some parameters allow partial searches using substrings of characters, representing the beginning, middle, or end of a string. For example, to search for “cupboard”, you could use the following substrings: “cup”, “boa”, or “ard”.
- If a command supports the dumping of output to a file, this is specified with -f.
- To separate multiple items of the same type, use the character “|”.
